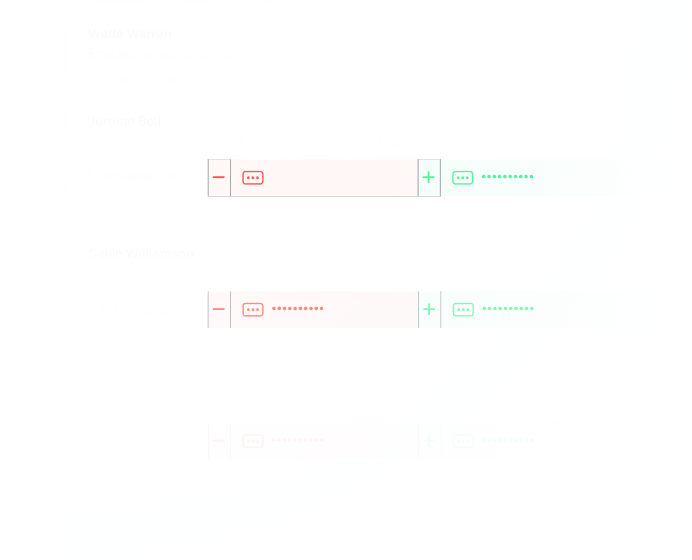
Implement Least Privilege Access
Our approach to least privilege access ensures that only the right people, can access the right secrets, at the right time.
No Access. No Entry.
Bolster security by enabling fine-grained control over who has access to what and when, maximizing compliance and minimizing risk.
Trusted and used by over 41,000 companies



"As a platform that manages customer compliance, our internal compliance requirements are of utmost importance. Doppler's regular and on-demand secret rotation, along with proper group and user provisioning featuring concrete scope and role-based access controls, elevated our secret management to a new level."

Peter Merkert
CTO & Co-Founder
A look under the hood
Doppler’s Mechanics
Enterprise-grade access controls designed to provide maximum security while maintaining flexibility and ease of management at scale.
Enter the new era of secrets management
Trusted by the world’s best DevOps and security teams. Doppler is the secrets manager developers love.